- Patched Tec-it Barcode Studio Enterprise V14.0.1.17931 Including Crack Download
- Patched Tec-it Barcode Studio Enterprise V14.0.1.17931 Including Crack Software
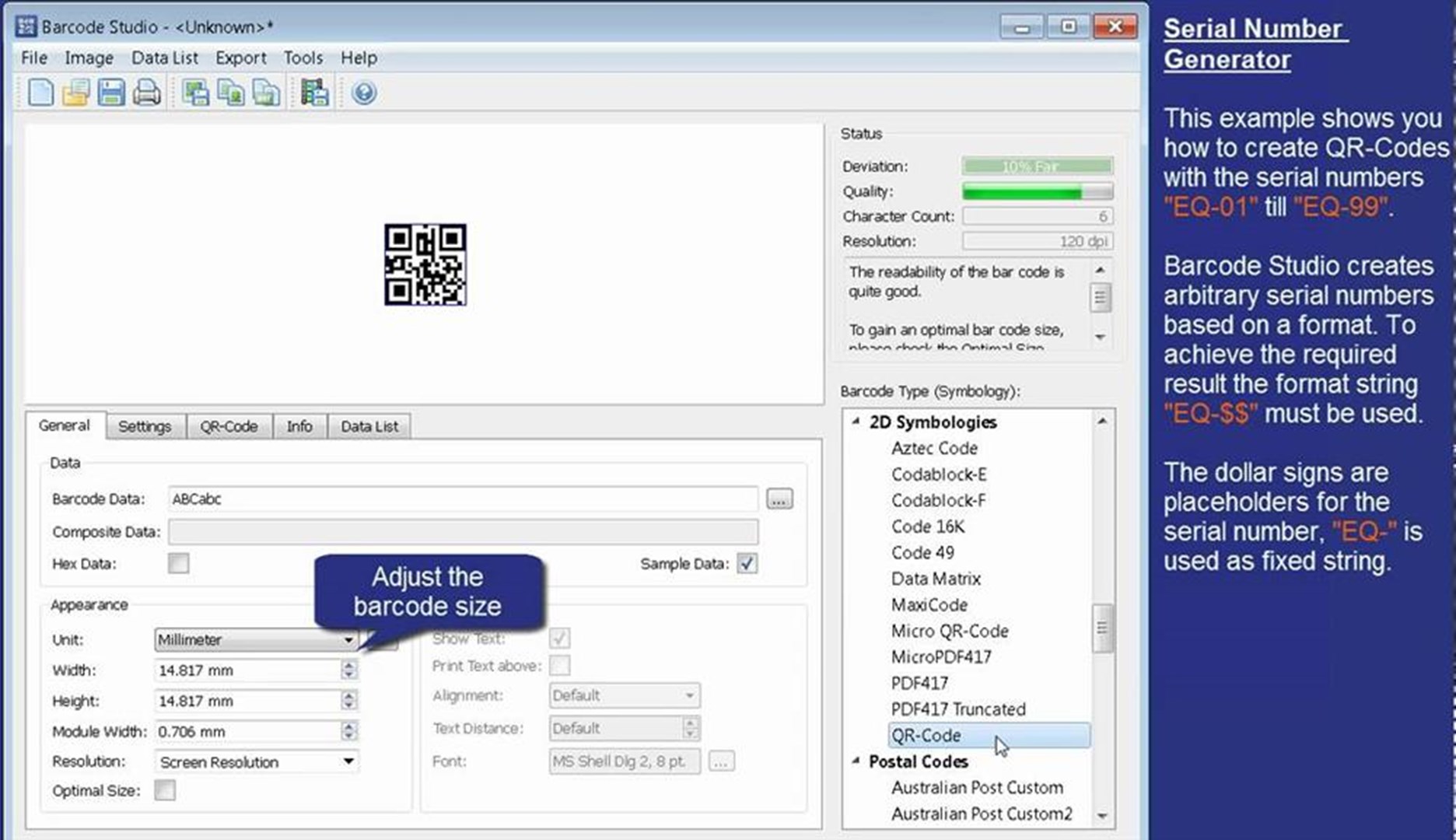
For the generation of barcode series Barcode Studio offers a range of possibilities: You can generate serial numbers automatically or import the barcode data from external files (TXT, CSV). Moreover, Barcode Studio offers a full-featured command line interface which allows batch operation (silent mode) and integration into third party. TEC-IT Barcode Studio Enterprise v14.0.1.17931 Including Crack h33t iahq7. With Barcode Studio you quickly create high-quality bar code images for pre-press requirements and desktop publishing applications.
Dinesat 9 full crack llave emulada farming simulator 2011 crack download iso microsoft kernel debug network adapter driver download windows 1041 whmsonic shoutcast admin pro nulled and 53 Cutlist Plus Platinum V 2009.5.5 download novel namaku hiroko pdf 50 Ek Tha Tiger Movie Telugu Download Online. C618e22409 Adobe Acrobat Pro DC 2015.017.20053 Incl Patch SadeemPC.rar. TEC-IT Barcode Studio Enterprise v14.0.1.17931 Including Crack Serial Key.
With regards to choosing a cloud supplier, the necessities you have and the assessment criteria you utilize will be one of a kind to your association. Notwithstanding, there are some regular zones of center amid any specialist co-op appraisal.
We have gathered these into 8 areas to help you adequately think about providers and select a supplier that conveys the esteem and advantages your association anticipates from the cloud.
Confirmations and Standards
Suppliers that consent to perceived guidelines and quality systems exhibit an adherence to industry best practices and models. While measures may not figure out which specialist co-op you pick, they can be exceptionally useful in shortlisting potential providers.
There are numerous measures and confirmations accessible. The picture above outlines a portion of the more typical associations that give guidelines, accreditations, and great practice direction.
All the more, for the most part, pay special mind to organized procedures, compelling information administration, great learning administration and administration status permeability. Likewise, see how the supplier wants to asset and bolster constant adherence to these principles.
Advancements and Service Roadmap
Advancements
Ensure the supplier’s stage and favored advancements line up with your present condition as well as help your cloud targets.
Do the supplier’s cloud designs, benchmarks, and services suit your workloads and administration inclinations? Survey how much re-coding or customization you may need to do to make your workloads appropriate for their stages.
Administration guide
Get some information about the supplier’s guide of administration advancement – How would they intend to proceed to enhance and develop after some time? Does their guide fit your needs in the long haul?
Vital elements to consider are duties to particular advances or merchants, and how interoperability is bolstered. Additionally, would they be able to show comparative organizations to the ones you are arranging?
For SaaS suppliers specifically, highlights, administration and combination guide is very attractive.
Contingent upon your specific cloud methodology, you may likewise need to assess the general arrangement of services that suppliers can offer. In the event that you intend to utilize isolate best of breed services from an expansive blend of supplier then this isn’t as applicable, however in the event that your inclination is to utilize just a couple of key cloud specialist organizations, it is essential for those specialist co-ops to offer a decent scope of good services.
Information Governance and security
Information administration
You may as of now have an information grouping plan set up that characterizes sorts of information as per affectability as well as strategies on information residency. In any event, you ought to know about administrative or information protection rules administering individual information.
In light of that, the area your information dwells in, and the ensuing nearby laws it is liable to might be a key piece of the determination procedure. On the off chance that you have particular necessities and commitments, you should search for suppliers that give you decision and control with respect to the ward in which your information is put away, prepared and oversaw. Cloud specialist co-ops ought to be straightforward about their server farm areas however you ought to likewise assume liability for discovering this data out.
Data security
Guarantee you evaluate the cloud supplier’s levels of information and framework security, the development of security activities and security administration forms. The supplier’s data security controls ought to be evidently chance based and plainly bolster your own security approaches and procedures.
Guarantee client access and movement are auditable by means all things considered and get lucidity on security parts and obligations as spread out in the contacts or business arrangements documentation.
Administration Dependencies and Partnerships
Seller connections
Watch the social dilemma - (2020) full movies & streaming online, free. Specialist organizations may have various merchant connections that are imperative to comprehension.
Surveying the supplier’s association with key sellers, their accreditation levels, specialized capacities and staff confirmations, is an advantageous exercise. Do they bolster multivendor situations and would they be able to give great cases?
Consider whether the services offered fit into a bigger biological system of different services that may supplement or bolster it. On the off chance that you are picking a SaaS CRM for example – are there existing mixes with back and showcasing services? For PaaS – is there a cloud commercial center from which to purchase complimentary services that are preconfigured to incorporate viable on a similar stage?
Patched Tec-it Barcode Studio Enterprise V14.0.1.17931 Including Crack Download
Subcontractors and administration conditions
It’s additionally essential to reveal any administration conditions and associations engaged in the arrangement of the cloud services. For instance, SaaS suppliers will regularly assemble their administration on existing IaaS stages, so it must be clear how and where the administration is being conveyed.
Now and again there might be an intricate system of associated segments and subcontractors that all have an influence in conveying a cloud benefit. It’s imperative to guarantee the supplier uncovers these connections and can ensure the essential SLAs expressed over all parts of the administration, including those not specifically under its control. You ought to likewise hope to comprehend the impediments of risk and administration disturbance strategies identified with these subcomponents.
Contracts, Commercials, and SLAs
Contracts and SLAs
Cloud understandings can seem complex, and this isn’t helped by an absence of industry norms for how they are built and characterized. For SLAs specifically, numerous language upbeat cloud suppliers are as yet utilizing superfluously confounded, or more regrettable, intentionally deceptive dialect.
Administration conveyance
Search for a reasonable meaning of the administration and expectations. Get lucidity on the parts and obligations identifying with the administration (conveyance, provisioning, benefits administration, observing, bolster, accelerations, and so on.) and how that is circulated amongst client and supplier. How is benefit openness and accessibility overseen and guaranteed (Maintenance, episode remediation, fiasco recuperation, and so forth.)? Zynga poker chips hack. How do these strategies fit your prerequisites?
Information strategies and insurance
Evaluate a supplier’s security arrangements and information administration strategies especially identifying with information protection directions. Guarantee there are adequate assurances around information get to, information area and purview, classification and utilization/proprietorship rights. Investigate reinforcement and versatility arrangements. Audit information change arrangements to see how transferable information possibly on the off chance that you choose to clear out.
Business terms
There is a heap of terms shrouded in the preparation module and your conditions will direct which are critical, however key contemplations include:
Authoritative and benefits administration, including to what degree the supplier can singularly change the terms of administration or contract.
What are the arrangements on contract restorations and exit or alteration see periods?
What protection strategies, certifications, and punishments are incorporated and what admonitions go with them.
Also, to what degree is the supplier willing to open their association to examining activities and consistency to approaches.
Legitimate Protections
Particular terms identifying with Indemnification, Intellectual property rights, Limitation of risk and guarantees ought to be standard terms in suppliers’ agreements. Be that as it may, the parameters identifying with each ought to be examined. Ordinarily, these securities are regularly the most fervently as clients hope to constrain their presentation to potential information protection claims following a rupture and in the meantime suppliers hope to confine their risk in instances of cases.
Cloud ads
Each cloud specialist organization has a one of a kind heap of services and evaluating models. Distinctive suppliers have interesting value points of interest for various items. Normally, estimating factors depend on the time of use with a few suppliers taking into consideration continuously use and rebates for longer duties.
Dependability and Performance
There are a few strategies you can use to quantify the unwavering quality of a specialist co-op.
In the first place, check the execution of the specialist co-op against their SLAs for the last 6 a year. Some specialist co-ops distribute this data, however, others should supply it if inquired.
Try not to expect flawlessness: downtime is unavoidable and each cloud supplier will encounter it eventually. It’s the means by which the supplier manages that downtime that matters. Guarantee the observing and revealing apparatuses on offer are adequate and can incorporate into your general administration and announcing frameworks.
Relocation Support, Vendor Lock-in, and Exit Planning
Merchant secure is a circumstance in which a client utilizing an item or administration can’t without much of a stretch progress to a contender. Merchant secure is generally the aftereffect of restrictive advances that are incongruent with those of contenders. Nonetheless, it can likewise be caused by wasteful procedures, or contract requirements, in addition to other things.
Cloud services that depend intensely on bespoke or remarkable exclusive segments may affect your transportability to different suppliers or in-house activities. This is particularly valid if applications must be re-architected keeping in mind the end goal to keep running on a specialist organization stage.
Business wellbeing and Company profile
Surveying the specialized and operational capacities of a potential provider is clearly vital, however, set aside the opportunity to consider the monetary wellbeing and profile of your shortlisted suppliers.
The most perfect or most aggressive cloud benefit is insignificant if the supplier doesn’t have a sound business. Ensure your fundamental suppliers are a solid match as long as possible.
Synopsis
Incorporate hard and delicate factors in your appraisal of forthcoming suppliers: perceive and approve both the accreditations and norms they cling to, yet in addition what their clients say in regards to them in the event that reviews and tributes.
Think long haul to maintain a strategic distance from secure – shirking of exclusive
1 | DropBox
2 | MediaFire Ibm spss download for mac free.
3 | 4Shared
4 | Google Drive
5 | SkyDrive
6 | iCloud
7 | Box
8 | Mega
Barcode Studio Enterprise v14.0.1.17931 | 11.06 MB
With Barcode Studio you quickly create high-quality bar code images for pre-press requirements and desktop publishing applications. Barcode Studio operates on its own, no additional software and no programming skills are required. Ready-to-use barcode templates support the creation of compliance bar-codes.
Barcode Studio helps you to create your own bar codes in perfect quality!
Barcodes as Bitmap or Vector Graphic

The required barcodes are created and parameterized directly on the screen, no special knowledge is necessary. The output of bar codes takes place directly on the printer, as a picture (BMP, GIF, JPG, TIF, PNG), as vector graphics (EPS, PDF, PostScript®) or to the clipboard.
Use the generated barcodes for your purposes immediately: Add the barcode graphics to image editing programs, databases, forms or arbitrary documents.
Guaranteed Barcode Quality
With the built-in quality preview feature of Barcode Studio you create perfect barcode images. The expected bar code quality is calculated in real-time by indicating the printing tolerance with respect to the output resolution (DPI). Thus you can qualify the bar code during design and avoid unreadable barcodes.
Serial Numbers, Data Import, Batch Operation

For the generation of barcode series Barcode Studio offers a range of possibilities: You can generate serial numbers automatically or import the barcode data from external files (TXT, CSV). Moreover, Barcode Studio offers a full-featured command line interface which allows batch operation (silent mode) and integration into third party applications (like Oracle Reports).

Preconfigured Templates
Barcode Studio contains ready-to-use barcode templates for EAN-13, EAN-8, UPC-A, UPC-E and Deutsche Post Premiumadress Data Matrix. All bar code settings are preconfigured to meet exactly the specification.
Mobile Tagging
The assistant simplifies especially the creation of 2d barcodes for mobile marketing and electronic business cards. You can generate mobile tagging barcodes for Facebook, Twitter, LinkedIn, sending SMS or even website visits as well as barcodes using the vCard or meCard format. If required URLs are shortened (and tracked) via Google or Bitly URL shortener services. The creation of GS1 barcodes is also simplified dramatically: just select the required application identifiers (AIs) - the data assistant takes care of the right formating (FNC1 insertions) automatically.
Patched Tec-it Barcode Studio Enterprise V14.0.1.17931 Including Crack Software
Barcode Label Printing
For printing generated bar codes the user can choose from predefined templates or define custom labels as required. Barcode Studio provides templates like Avery or Avery/Zweckform.
Homepage
Download Links
Letitbit
Turbobit
Uploaded